Enterprises today are leveraging and heavily investing in developing cutting-edge enterprise apps to automate workflow processes and drive business efficiency. Enterprise apps offer significant benefits, including improved productivity, scalability, better customer service, and reduced operational costs. However, one major concern associated with the usage of enterprise apps is data security.
In 2023, the average financial impact of a data breach in the USA, as reported by Statista, stood at $9.48 million.
Data security breaches pose a serious threat to enterprises that significantly contribute to the loss or misuse of a company’s sensitive information. It also compromises financial data and imposes privacy threats. Therefore, enterprises need to stay vigilant against security breaches to protect their critical business data, systems, and customer information.
Nevertheless, the best way to secure enterprise data is to adhere to the security best practices and trends throughout the enterprise application development process. In this article, we’ll delve into exploring the intricacies of what security by design means and its best practices. Moreover, we’ll learn how to mitigate enterprise app security vulnerabilities by implementing security best practices and standards/frameworks.
Key Takeaways
- Security by Design revolves around the concept of integrating security considerations at every stage of the development process to mitigate risks proactively.
- Secure coding practices, such as strong access control, MFA, regular security audits, and proactive vulnerability management are crucial for minimizing the risk of exploitation and ensuring enterprise application integrity.
- Adherence to industry-recognized security standards and frameworks, such as OWASP, PCI DSS, and ISO 27001 enhances overall security posture and demonstrates a commitment to data protection.
- Utilizing security best practices also helps enterprises stay vigilant against evolving security threats and vulnerabilities.
- Implementing Helmet middleware significantly enhances Express.js application security by enforcing critical security headers and protective measures.
Table of Content
- What is Security by Design?
- Web Security by Design Best Practices for Enterprise Applications
- Web Security Best Practices to Mitigate Common Enterprise Application Vulnerabilities
- Web Security Standards and Frameworks
- Web Security Trends in Enterprise Application Development
- Example: Node.js & Express.js with Helmet
- Conclusion
What is Security by Design
The process of designing a system by incorporating the best security measures from the initial planning and design phase and continuing throughout the entire enterprise app development lifecycle to make it as secure as possible from the beginning is known as ‘Security by Design'. When enterprises lay the core foundation of their enterprise app on security by design, they can make the app less prone and susceptible to data vulnerabilities and security threats.
Web Security by Design Best Practices for Enterprise Applications
Here are the security-by-design best practices that help in building highly secure and robust enterprise applications from start to finish.
Early Integration of Security
Security is one of the crucial aspects of enterprise apps and that’s the reason why now it's become more than necessary for enterprises to consider the security by design approach. Enterprises can effectively combat evolving cyber threats by considering security from the very start of their enterprise app development and throughout the lifecycle. Using security by design helps detect and prevent potential security risks that might cause serious damage to the enterprise data if left unaddressed or unidentified in the early stages of development.
Secure Coding Practices
Developers must instill the habit of adhering to security coding best practices while writing code to ensure the developed app withstands security tests and can mitigate common vulnerabilities. Peers can review each other’s code or utilize automated tools to seamlessly identify if the written code follows the best coding practices and is resistant to security threats. For example, developers can use strncpy() function instead of strcpy() to overcome buffer overflow issues. If developers don’t focus on catching this coding vulnerability, then hackers can easily exploit and gain unauthorized access to enterprise systems.
Vulnerability Management
Enterprise apps are vulnerable to data breaches and cyber attacks that require continuous, automated, and proactive approaches to mitigate them effectively. Vulnerability management is the five-step management lifecycle, which includes assessing, prioritizing, acting, reassessing, and improving. It helps to identify and prevent cyber security vulnerabilities in enterprise systems and the software that runs on them before hackers can exploit them.
- Assessing: The first stage involves assessing and scanning each asset for vulnerabilities to identify, which assets are at risk and need patching or further remediation.
- Prioritizing: After assessing and scanning different assets, determining their level of risk helps in prioritizing the ones that are potentially weak or require immediate attention.
- Acting: Now, implementing mitigation measures such as patches, updates, configuration changes, or security controls helps in addressing critical vulnerabilities identified in the second stage.
- Reassessing: After implementation, it's essential to reassess systems and applications to ensure vulnerabilities have been adequately addressed.
- Improving: To proactively defend against potential vulnerability, enterprises must regularly examine and reevaluate the strategies implemented and continuously evolve to improve overall security.
Implementing Robust Security Measures
From the early development stage, enterprises must implement robust security measures including, strong authentication mechanisms, encryption protocols, access controls, regular security audits, and vulnerability assessments to detect and prevent critical security issues. By staying vigilant, enterprises can safeguard sensitive business data and maintain its integrity, and confidentiality even when adopting enterprise mobility solutions.
Web Security Best Practices to Mitigate Common Enterprise Application Vulnerabilities
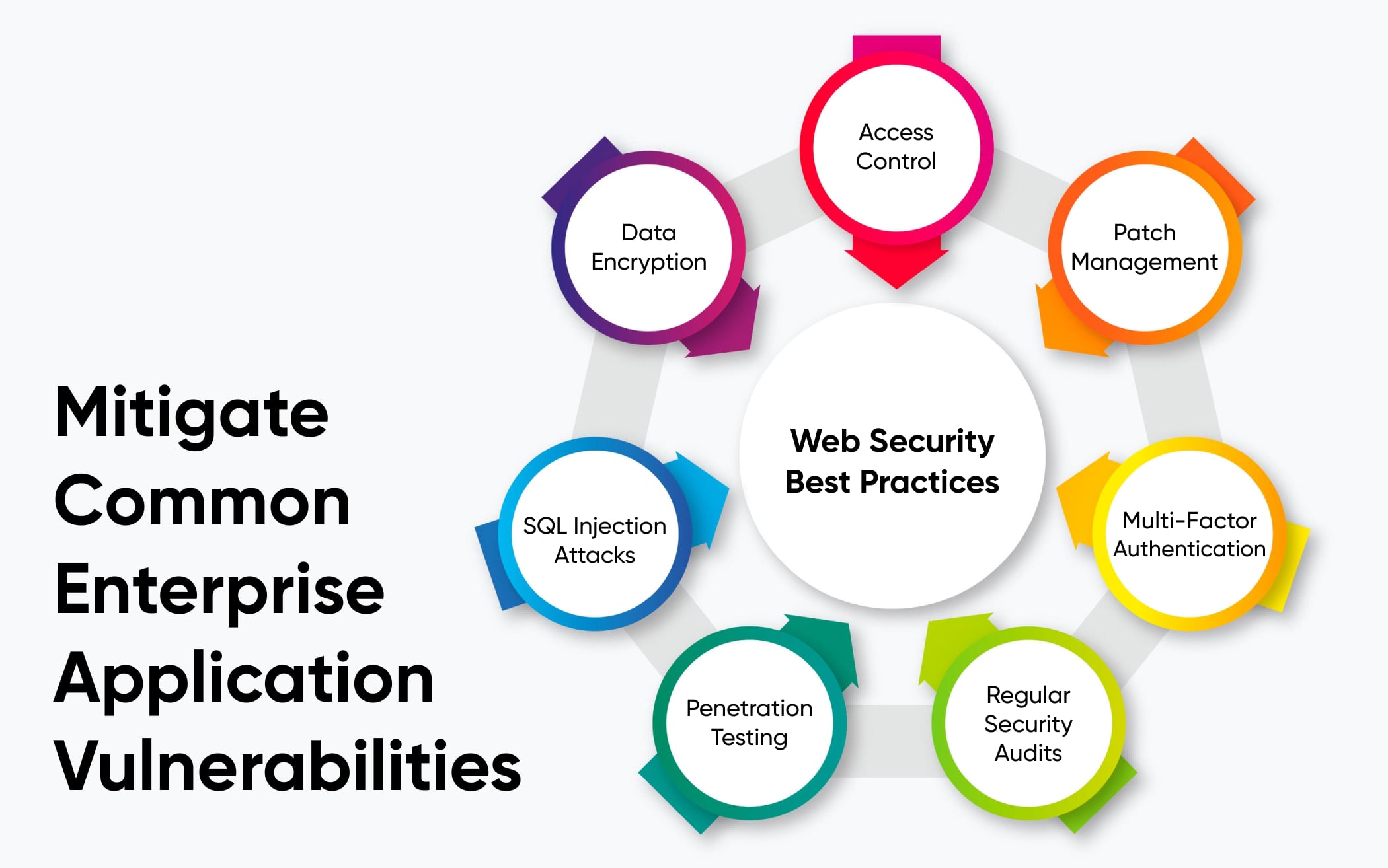
Enterprises may encounter various security vulnerabilities in their enterprise application that can pose serious threats to sensitive business data and operations. Below, we’ve listed the security best practices that help you mitigate the common security vulnerabilities in enterprise apps.
Access Control
Broken access control is why enterprises fall victim to cyber attackers who can easily intrude on the system to steal, expose, alter, or destroy sensitive information. Enterprises, however, need to implement proper authentication and role-based access control mechanisms to restrict system access based on users' roles and responsibilities within the organization, thus reducing the risk of unauthorized access attempts and data breaches.
Patch Management
Patch management involves regularly updating the enterprise application with the latest security patches and fixes issued by software vendors to address known vulnerabilities and weaknesses to prevent the risk of exploitation by attackers. Enterprises must consider patch management as a regular maintenance process that also boosts the enterprise app's operating performance and keeps it running in a top-notch condition.
Multi-Factor Authentication (MFA)
Inadequate authentication measures like weak passwords or compromised credentials make it easy for intruders to gain unauthorized access to user accounts. Using complex passwords along with implementing multi-factor authentication (MFA) proves to be extremely beneficial to overcome this challenge. MFA with its extra layer of security, requires users to go through several authentication checks, including passwords, biometrics, or security tokens to get secure access to their accounts.
Regular Security Audits
When enterprises conduct regular security audits, they can identify security vulnerabilities, weaknesses, and potential threats within their enterprise application to ensure that business-sensitive information is protected against potential threats. Moreover, they can evaluate the effectiveness of existing security measures, detect security gaps, and recommend improvements to mitigate security risks.
Penetration Testing
Penetration testing, also known as ethical hacking, involves simulating real-world attacks on systems and networks to identify vulnerabilities and weaknesses that could be exploited by malicious actors. Enterprises can conduct regular penetration testing and implement effective security techniques to ensure the enterprise application is secure against potential security weaknesses and evolving threats.
SQL Injection Attacks
Hackers can easily manipulate data or gain unauthorized access by inserting malicious SQL queries into the input field of enterprise applications. To mitigate SQL injection attacks, developers should use parameterized queries or prepared statements instead of concatenating user input directly into SQL queries. Additionally, input validation and data sanitization techniques should be implemented to ensure that only safe and expected data is processed by the application.
Data Encryption (at Rest and in Transit)
Encryption scrambles data to make it unreadable without the proper decryption key. Data should be encrypted both when stored (at rest) and when transmitted over networks (in transit). For example, enterprise apps might use SSL/TLS encryption for secure communication between clients and servers, and encrypt sensitive data stored in databases using algorithms like AES. Encryption ensures that even if attackers gain unauthorized access to enterprise data, they cannot decipher it.
Web Security Standards and Frameworks
Adhering to industry-recognized security standards and frameworks is crucial for organizations to ensure the protection of sensitive information, maintain customer trust, and mitigate the risk of security breaches. Here are the three different security frameworks that enterprises can utilize in the development of secure enterprise applications.
OWASP (Open Web Application Security Project)
OWASP offers a comprehensive set of guidelines and resources useful for developing secure web-based enterprise applications and protecting them from evolving cyber-attacks. Security analysts can address common vulnerabilities such as SQL injection, cross-site scripting (XSS), and authentication flaws within the enterprise app by following OWASP best practices.
PCI DSS (Payment Card Industry Data Security Standard)
PCI DSS is a set of policies implemented for security purposes, including the protection of credit and payment card data and transactions. Compliance with PCI DSS helps enterprises secure payment card data, prevent fraud, and maintain the integrity of transactions, thereby safeguarding the financial data of both customers and businesses.
ISO 27001 (Information Security Management)
ISO 27001 is an information security standard that comprises a set of guidelines to implement and manage ISM. By adopting ISO 27001 standards, enterprises can incorporate robust security policies, procedures, and controls to protect their sensitive data, manage risks effectively, and demonstrate a commitment to information security best practices.
Web Security Trends in Enterprise Application Development
The security landscape continuously evolves with the latest security trends and best practices to ensure the app stays vigilant against rapidly evolving threats and vulnerabilities. Let's take a look at the top security trends that can be implemented in enterprise apps to maintain robust security protection.
Shift-Left Security
The process of embedding security during the early stages of the enterprise application lifecycle is known as shift-left security. This proactive approach helps improve code quality and reduce costly remediation efforts later in the deployment process by identifying security breaches, vulnerabilities, and data leaks from within the beginning of the enterprise application development. Thus, enterprises must practice security testing from the initial stage and continue throughout the development lifecycle to enhance the overall security posture of the enterprise application.
DevSecOps Integration
Development security operations (DevSecOps) is one of the best practices to follow while developing enterprise applications, as it aims to integrate security measures throughout the entire software development lifecycle, from design and coding to testing and deployment. It takes care of security vulnerabilities as soon as they appear, before they are deployed into production when fixing them is simpler, quicker, and less expensive. Moreover, it enables continuous security monitoring and rapid feedback to remediate security vulnerabilities and build highly secure enterprise applications.
Cloud Security Considerations
Cloud security is in growing demand nowadays as it helps enterprises safeguard critical data in the cloud environment. Understanding and implementing appropriate cloud security measures in enterprise apps mitigate risks associated with data breaches, unauthorized access, and service disruptions. Therefore, enterprises must leverage cloud security features, including encryption, multi-factor authentication, network segmentation, and real-time monitoring to improve data protection and ensure regulatory compliance.
API Security
As APIs play an increasingly central role in enterprise applications, securing APIs against threats is paramount in enterprise applications. This involves implementing techniques such as API gateways, access control mechanisms, encryption, and authentication to protect APIs from unauthorized access, data breaches, and malicious attacks. Additionally, implementing robust API security measures leads to seamless and secure integration between enterprise applications and other third-party services.
Example: Node.js & Express.js with Helmet

Helmet is a security middleware for Express.js, a popular web application framework for Node.js. It helps secure Express.js applications by setting various HTTP headers to protect against common web vulnerabilities, including cross-site scripting (XSS), cross-site request forgery (CSRF), clickjacking, and other security vulnerabilities by setting appropriate headers.
Enterprises can utilize Helmet within their Express.js application to add an extra layer of protection without manually configuring each security header. In essence, Helmet acts as a layer of defense by configuring HTTP headers to improve the overall security posture of Express.js applications.
Security Benefits Offered by Helmet
Let’s dive into discovering the top security benefits offered by Helmet middleware.
- Content Security Policy (CSP): CSP Mitigates cross-site scripting (XSS) and data injection attacks by indicating, which URLs the browser ought to accept as legitimate providers of executable scripts.
- Hide Powered-By: Removing the X-Powered-By HTTP makes it harder for attackers to target specific server types and exploit known vulnerabilities.
- HTTP Strict Transport Security (HSTS): An extensively adopted standard HSTS makes sure that users' browsers always connect to websites over HTTPS.
- X-Download-Options: It seamlessly controls how web browsers handle downloadable content, which reduces the risk of malicious file execution.
- X-Content-Type-Options: This security benefit of Helmet prevents MIME-type sniffing, ensuring that browsers interpret the content as specified to enhance security against content-based attacks.
- HTTP X-XSS-Protection: The HTTP X-XSS-Protection response header prevents pages from executing when they detect any suspicious cross-site scripting (XSS) attacks in enterprise apps built with Express.js.
- Referrer Policy: Allows developers to control how much information is included in HTTP referrer headers to reduce the risk of information leakage between websites.
- Expect-CT: Helps impose certificate transparency to detect and mitigate misissued SSL certificates to instill trust and security in SSL/TLS certificates.
- Permissions Policy: Helmet also enables developers to control browser permissions for features like camera access that ultimately reduce the risk of unauthorized data access.
- Cross-Site Scripting (XSS): Enterprises can prevent the injection of malicious scripts into web pages to protect users and data from potential exploitation and manipulation.
Conclusion
Security is one of the most crucial aspects of enterprise applications that requires the implementation of robust security measures and adherence to security best practices and trends. In this blog post, we’ve discovered how security plays a vital role in proactively shielding enterprise applications against emerging threats and security risks by following the security best practices, including strong access control, MFA, secure coding practices, regular security audits, robust data encryption, and more.
Developers can mitigate common security vulnerabilities like SQL injection attacks, malicious attacks, and sensitive data exposure with the use of security best practices, standards, and frameworks. Further, staying updated with up-and-coming security patterns and trends ensures they remain ahead of potential threats and vulnerabilities.
However, enterprises must also work on conducting user education and awareness programs to empower employees to recognize and respond to security threats effectively. These programs help cultivate a security-conscious culture within the organization to improve overall security resilience.











